RPC_S_Server_Unavailable error (0x6ba) and Microsoft Exchange is unavailable.
Filed Under IT Tipz & Trix, Sighs
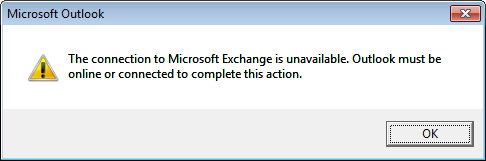
This post probably falls more under the doh! category than anything else but it might still be useful if anyone else suffers from the same apparent brain failure as I did 🙂 When setting up a remote user to use Outlook and was struggling massively to get it to connect. Every time Outlook would give me the following error stating that Outlook must be online or connected to complete this action.
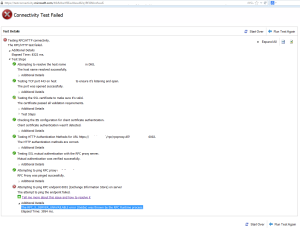
Could something have changed that I was unaware of? I tried testing it with the Exchange Connectivity Tester (which is a brilliant troubleshooting tool btw) and that failed too with the horrible “The RPC_S_SERVER_UNAVAILABLE error (0x6ba) was thrown by the RPC Runtime process” error.
Google advice on the 16000+ results for that term ranged from disable IPv6 to registry edits on the server. But since it was only this one user that had issues, I didn’t think we needed to go that far. I could happily connect to ports 6001,6002 and 6004 and every other remote user was having no issues. Then it occurred to me, like a 100 year old lightbulb slowly, so very slowly, dispelling the dark fugue of confusion – this looks like a DNS error. Why is it unable to ping the server? What is it trying to ping? OWA works find for the user so it’s not an account issue. The problem – I had entered the external server name in the Outlook Account Settings (:facepalm:).
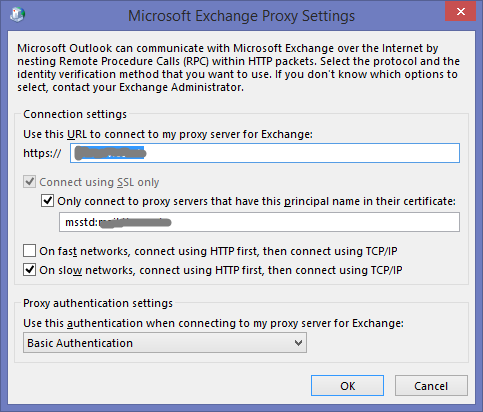
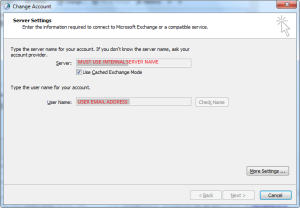
The proxy server you enter for RPC over HTTPS for the Exchange account details here :
is NOT the same as the address you enter for your server here :
Once I changed the Outlook Config to point to exchange.contoso.local – BOOM! Problem solved. And a quite shocking amount of “OMFG I wasted so much time on this, what a numpty I am” 🙂
About this Post
Permalink | Trackback |
|
Print This Article | Leave a Comment
The Case of Metasploit and the Facebook Cookies.
Filed Under IT Tipz & Trix
Or How I Started My Metasploit Scripting Journey
I have been using MetaSploit for a while now and have slowly got comfortable enough with it to start tinkering under the hood so to speak. Most of this has been driven by a desire to get the most out of the trial version of Cobalt Strike which is hands down one of the most awesome pieces of software I have played with in a while.
Whilst Cobalt Strike’s built in browser pivoting is awesome, I believe it is most useful on a reliably exploited box, rather than one that might only connect occasionally like a laptop. There are many wonderful post modules already supplied with the Metasploit framework for gathering credentials, but I couldn’t find an out of the box solution for grabbing Windows 8 cookies (enum_ie for example won’t work on a Win8 box) so I thought I would go about writing my own.
After all – how hard can it be!!
A little research shows that Windows 8 cookies are stored in %USERPROFILE%\AppData\Local\Microsoft\Windows\InetCookies and %USERPROFILE%\AppData\Local\Microsoft\Windows\InetCookies\Low in TXT files.
With my test target exploited I thought the best approach would be to search those folders and download each TXT file so we could have a complete copy of all of the IE Cookies for the logged on user.
What follows is many different approaches, one ultimately successful and IMHO a good demonstration of thinking outside the box to solve issues when you are on your own! If anyone knows of a good place for discussing newbie level Metasploit issues and being guided through the process – please let me know. Always keen to learn!
About this Post
Permalink | Trackback |
|
Print This Article | 2 Comments on The Case of Metasploit and the Facebook Cookies.
 RSS feed
RSS feed